UK: 03330 156 651 | IE: 01263 5299
Your Employee Passwords are Probably Up for Sale on the Dark Web
Lucky for you, we can see which ones. Enter your details below to get a free report on your business’s vulnerabilities.
Yellowcom Software Powered by Industry Leaders in Business Cyber Security




SMALL BUSINESS CYBER SECURITY
You Can't Fix What You Can't See
Billions of usernames and passwords have been stolen from big companies and leaked online. Hackers buy lists of credentials to break straight in to businesses just like yours. Unless you are Dark Web Monitoring – You’ll never even know your data is out there.
If your staff use the same password for streaming services as they do for work accounts, you are at risk.
Your employees aren’t lazy – they’re just creatures of habit. Despite increasing rates of cybercrime in the UK and Ireland, some shocking statistics still persist.
80%
of people reuse passwords between multiple websites
50%
of employees admit to using personal passwords for work accounts

A Tiny Leak Can Become a Major Breach
The Leak
An employee uses their work email to sign up to a useful subscription newsletter. That site gets hacked. Your data is now exposed.
The Sale
The hacker sells the email/password combo to a malicious party on the Dark Web for £5.
The Breach
Bots try that password on your Office 365. Since the employee reused the password, the hacker is in.
ADMIN
is still the most commonly used password in the UK and Ireland.
Small Business Cyber Security
We Watch the Bad Guys so You Don't Have To
Yellowcom scans the hidden parts of the internet where criminals buy and sell data. We monitor your business domain 24/7. If an employee’s password appears on a black market list, we tell you immediately.
We Monitor
Hidden chat rooms, private websites, and obscured peer-to-peer networks.
We Find
Stolen passwords, compromised email accounts, and leaked data.
We Alert
You get a notification the moment we find any of your exposed data.
Cyber security solutions for small businesses
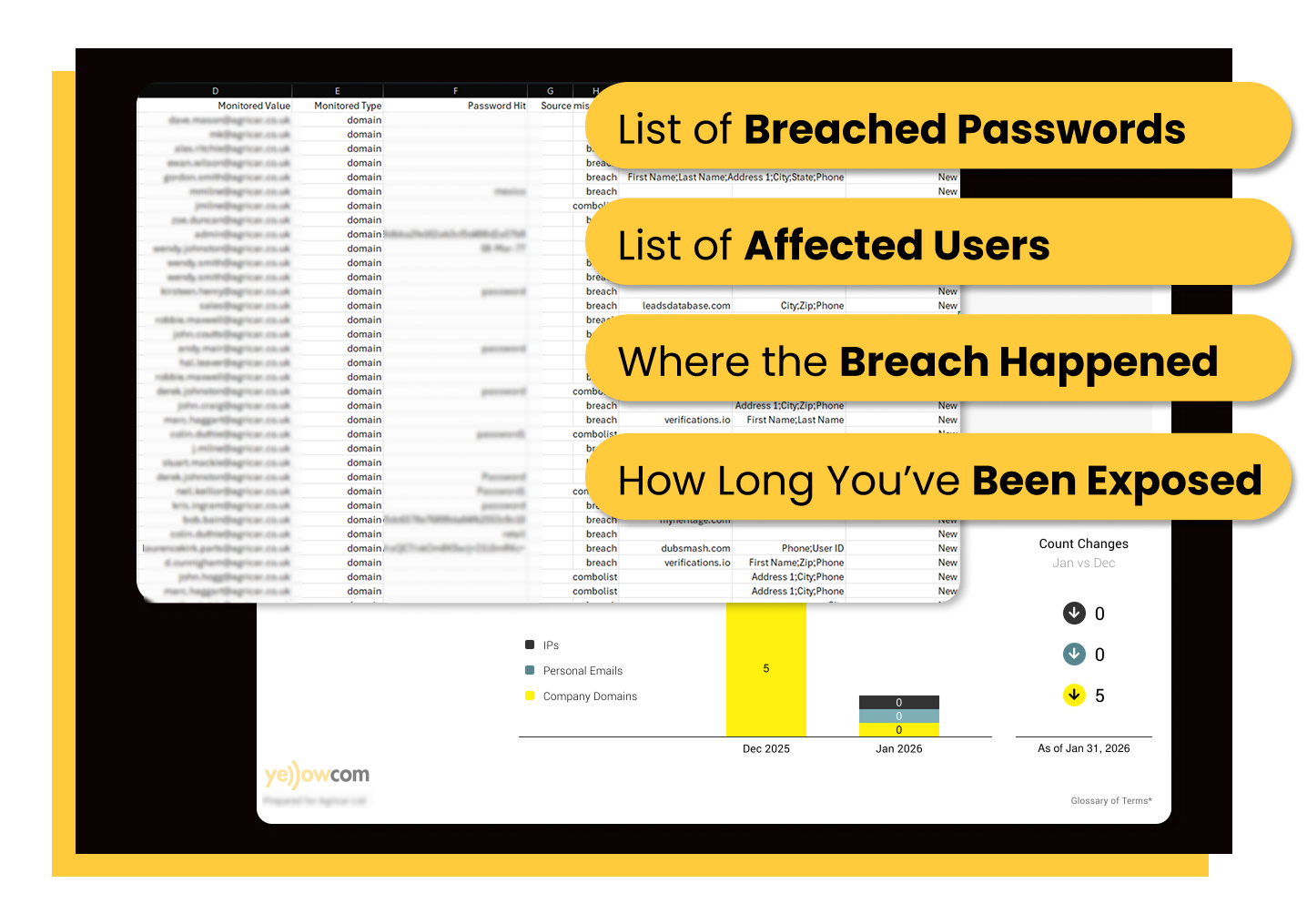
What's in Your Report?
You’ll get a PDF listing your exact compromises – who’s at risk, what website the breach occurred from, and how long the data’s been available.
This report is a detailed blueprint showing you exactly where you need to lock down your employee credentials before a major breach.
Small business IT Support
Take the First Step to Securing Your Business
Step 1: Submit your details in the form provided.
Step 2: We run the scan. We check your domain against databases of stolen credentials.
Step 3: Get your report. We email you a simple list showing exactly which email addresses and passwords are currently exposed.
Submit your Details to Start your Dark Web Domain Breach Scan
Rated 5 Stars by Small Businesses
EXCELLENTTrustindex verifies that the original source of the review is Google. Keeley went above and beyond to help me with the problems I was having, even after helping I got a follow up call to make sure everything went well. service was A++Posted onTrustindex verifies that the original source of the review is Google. Spoke to Natalie in the technical team and she resolved my issue very quickly in a professional manner 5 starPosted onTrustindex verifies that the original source of the review is Google. I had a technical issue and spoke to Natalie in the tech support team who resolved our issue in a professional manner and promptly an asset to the companyPosted onTrustindex verifies that the original source of the review is Google. We are a GP surgery and fairly new customers to Yellowcom and I have to say, we have no issues, they are reliable and efficient if and when we need to consult with them, I would highly recommend them to any business and Rob Campbell our account manager is greatPosted onTrustindex verifies that the original source of the review is Google. Yellowcom are a great company who provide a great service. All the staff are always pleasant and helpful. We've been with yellowcom for 18years and would highly recommend.Posted onTrustindex verifies that the original source of the review is Google. I can honestly say that we have been helped in every way from filing in form and every query we have had has been dealt with. We could not speak highly enough of this company. Thus we would them .recommend them to anyone.Posted onTrustindex verifies that the original source of the review is Google. Excellent service from Ross in accounts.Posted onTrustindex verifies that the original source of the review is Google. Had a great review of services with Rob Campbell today. Easy to discuss small issues and focus on what's working well. Looking forward to what's next!Posted onTrustindex verifies that the original source of the review is Google. Thank you to Yellowcom and Peter Millen for all your support in 2025.
Common Questions about Dark Web Monitoring for Small Businesses
Cybersecurity can feel complicated, but keeping your business safe shouldn’t be. We have stripped away the jargon to give you simple, honest answers about how our Dark Web scan works.
We believe every business in the UK and Ireland deserves to know if their data is at risk—without the hard sell.
Don’t see your question here? Reach out directly to your local Support Team.
Is this really free?
Yes. We are a local IT company in Belfast, Glasgow, and Dublin. We offer this report for free because we believe every business deserves to know if they are exposed. There is no obligation to buy anything.
Will you see my actual passwords?
We only see that a password exists in a leak (e.g., a hash or encrypted string). We never see or store your actual login details. Your privacy is 100% protected.
What happens if you actually find something?
We will email you a confidential PDF report. It lists exactly which email addresses were part of a breach and when it happened. You can then force a password reset for those staff members immediately.
Do I need this if I have 2FA?
Yes. While 2FA is a great layer of defense, it is not unbreakable. Hackers can trick staff into approving logins or use stolen passwords on other accounts where 2FA isn’t active. It is always safer to know if a password has been compromised so you can change it immediately.
How often do you scan for threats?
24/7/365. Cyber criminals don’t work 9-to-5, so neither does our system. We monitor the Dark Web in real-time and alert you the moment a new threat is detected, day or night.


